Phishing
The always evolving email scam
Lorem Ipsum dolor site amert engding to amert sigmafntic dolorsite is amiono hmrtamio.
- Compliance Management
- Real-time Monitoring
- Scalable Solutions
- User-Friendly Interface
What is Phishing?
Phishing is a type of social engineering where an attacker sends a spoofed email designed to trick a victim into revealing sensitive information, or to deploy malicious software on the victim's infrastructure.
Advanced Security Content Delivery for Network.

91% of
cyberattacks start with a phishing email
95% of all cyber attacks begin with a phishing email to an unexpected victim
[ source: yourdmarc ]
60%+ of
companies go out of business
More than 60% of businesses close permanently within 6 months of a cyber-attack.
[ source: yourdmarc ]
Over 200K
nique Phish Sites
In 2021, 214,345 unique phishing websites were identified, with recent phishing attacks doubling since early 2020
[ source: yourdmarc ]
 ATTACK EXAMPLE
ATTACK EXAMPLE

What Does phishing looks like?
Phishing emails are an extremely successful method of stealing information for cybercriminals. Typically, a bad actor will impersonate a recognizable brand or a person known to the victim, to trick a them into clicking on a link or attachment. This can lead to personal financial and/or data theft.
Mass Phishing campaigns are a numbers game. By leveraging the ubiquity of a brand like Netflix, the email will likely appear relevant to a sizeable portion of recipients. Attacks like this can easily be sent to a million recipients. A success rate of only 0.5% still results in 5,000 infections or stolen credentials that be used in future, more-targeted scams, making these phishing campaigns a very worthwhile exercise for bad actors.
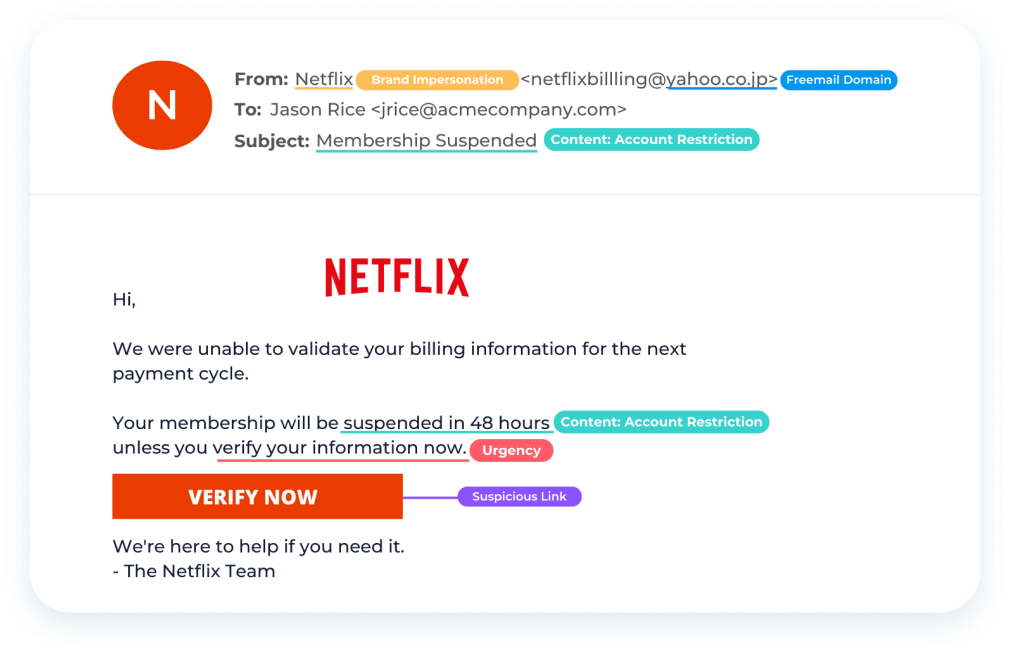

Brand Impersonation
With the display name “Netflix” the attacker is attempting to masquerade as Netflix. On a mobile device, the recipient will likely only see the display name.

Contains a Deadline
The attacker creates a sense of urgency by telling the user they have 48 hours to comply.

Credential Theft
The call to action links to a fake login page designed to steal the user’s credentials.
certainty in sender authenticity
FTE expenses saved annually
Projected cost of cybercrimeby 2025
Number of malicious emailssent daily
of data breaches caused by phishing attacks

Subscribe for Updates
Join our notification service for alerts on new eBooks and the latest industry news. Sign up today to stay informed and boost your email security knowledge!
How Does Mesh Protect Against Phishing?

URL Protect
All links in the email are subjected to scanning against real-time threat feeds for known and unknown malicious sites as well as fake login pages and phishing sites. Links to unknown or suspicious objects are sandboxed.

Attachment Sandboxing
Unknown and potentially malicious attachments are detonated in a virtual environment to determine their behavior, protecting against never-before-seen, zero-hour threats like polymorphic malware.

Antimalware Engines
Mesh uses a combination of commercial and proprietary engines to perform signature and heuristic-based scanning in order to detect known and unknown, types of malware such as viruses, ransomware and trojans.
Our Happy Clients
1000+Emails
143,887Compliant
136,696Failures
5,399Countries
60+Domains Analyzed
27,000+Used and Trusted by Industry Leaders


“YourDMARC secures emails, saves our time. Our small healthcare practice struggled with email security. YourDMARC's DMARC/DKIM combo and real-time alerts are a lifesaver! HIPAA compliance is a breeze now, and their support team is top-notch. ”



“YourDMARC responds quickly to the needs of our business. I've worked with many companies and what is most impressive and unique about yourDMARC is their ability to act as a true partner with aligned interests and not just one party to a transitional relationship. ”
Nick Kitchin CEO at Cumulus Energy Storage



“ Give 5 Star to this product and recommend this tool to the domain professional email owners. Good use of artificial intelligence and give only required alerts and information. I will recommend this product to domain and professional email owners.”
Deepak CTO at Softuvo Solutions










